"Everything is a file" is one of the basic philosophy of Unix/Linux. Directories, character devices, block devices, sockets, etc. exist in the form of files in Unix/Linux. Faced with many files, how to understand and manage their read, write, and execute permissions?
Under Windows, you can right-click the file to view the file permissions in the property bar. Is the file "philosophy" under Linux the same as Windows? We analyze from the following points.
1 . The role of file permissions
The setting of file permissions is to protect the security of the system and user data. For users, the most important thing is the privacy and security of data and files. From system administrators to ordinary users, from file attributes to file special encryption, all around a theme: rights management. If a critical file is accidentally written, the data is lost, and the system crashes.
Take the /proc directory file in the root directory as an example. This file is a virtual file system provided by the Linux kernel. It can access the internal data structure of the kernel and change the kernel settings. Among them, swaps is the use of swap space, tty saves tty device information, version Linux kernel version and gcc version. We can find that all the files closely related to the system are read-only, even for the root user.

Figure 1 Some files under /proc
2 . Division of file permissions
Permission management under Linux can be roughly divided into three parts from the perspective of visitors, namely users, user groups, and administrators. As shown in Figure 2, open the file list details in the current user directory. Most of the time we use this command to focus only on the right half of the information, such as file name, date, size, etc. The left part shows the permission information of the corresponding file.
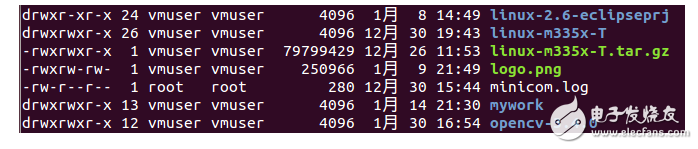
Figure 2 file attribute details
The Linux system has strict management of user permissions. As shown in Figure 3, the permissions of a file can be divided into three parts: permissions for the file owner, permissions for the user group where the owner is located, and permissions for other users. Among them, the user group (group) is a collection of users with the same characteristics.
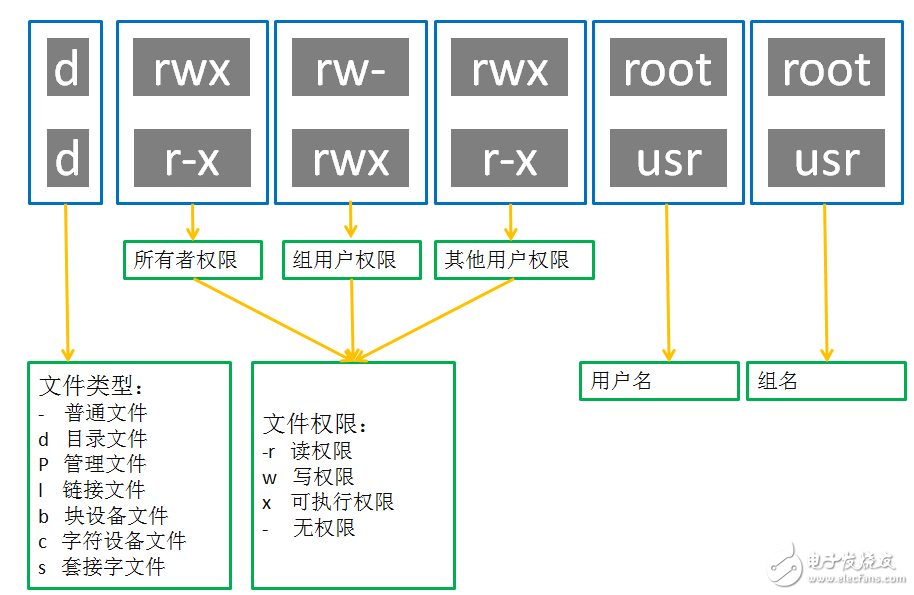
Figure 3 file permissions
The user and user group information are in the passwd and group files in the /etc directory, which can be directly read using the cat command.
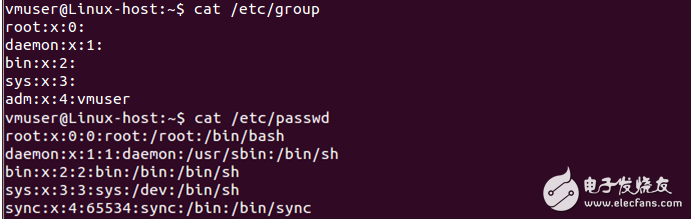
Figure 4 User/user group information
3. How to change file permissions
Linux provides the chmod command for changing or setting file permissions. The command format is shown in Figure 5. Remove the other user permission executable attributes of the hello file: vmuser@Linux-host: hello$ chmod ox hello. If u/g/o is set at the same time, it can be expressed by a, for example, adding all user executable permissions for hello: vmuser@Linux-host: ~$ chmoda+x hello.
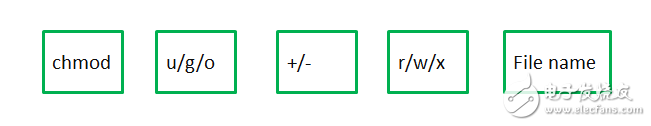
Figure 5 Change of file permissions (1)
Earlier we said that Linux file permissions management is a "philosophical beauty", the chmod command also provides a more indirect way of use. As shown in Figure 6, r, w, and x correspond to the numbers 4, 2, and 1, respectively, and the sum of the numbers represents the set of authority values. For example, rwx can be represented by 7 and rx can be represented by 5. If you want to set the hello file to the most relaxed permissions, you can directly use the command chmod 777 hello.
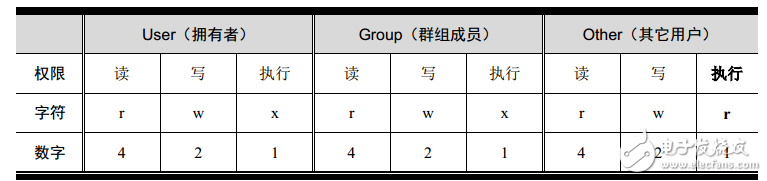
Figure 6 File permission changes (2)
So besides creating the file first and then modifying the permissions, is it possible to directly create files with specific permissions? The answer is yes, we can manage the default permissions of corresponding users by modifying the value of umask. You can directly enter umask to get the default value of the current user's permissions, of course, you can also use umask=xxx to modify it. In addition, if you want to set the umask value permanently, you can modify ~/.bashrc or. /bash_profile. The value of Umask does not correspond to the permission of the file. Readers who are interested can refer to relevant information.
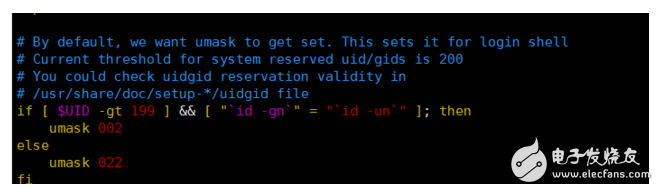
Figure 7 user default permissions change
4. How to protect important files
The protection of files can be started from the perspective of quantity: file rights management and timely backup of files.
In terms of permission management, you cannot change the file permissions at will, such as directly chmod 777 filename. Taking the working log file of the system or APP as an example, it can only be read by most log-in users. If you overwrite it, the log information will be permanently lost. In complex multi-user collaborative systems, single user permissions and group user permissions should be strictly managed, and root user permissions should be used with caution.
Figure 8 read-only log file
For standard rootfs, it is not recommended that ordinary users directly change it, and give it read-only permission directly when uboot mounts the file system. Assigning the last item of bootargs to "ro" is read only. If you need to temporarily modify to read-write mode, you can use mount -o remount, rw /, for temporary modification to read-write mode, try to avoid modifying the uboot code.
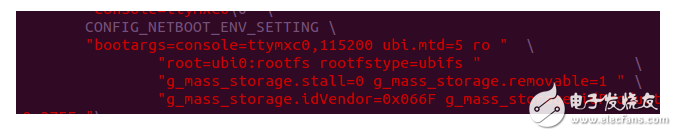
Figure 9 File system permission changes
Another means of protecting important files when backing up files is not guaranteed to be foolproof under strict permission management mechanisms. Important files can be automated and regularly backed up using scripts. If necessary, files can also be saved to other physical storage media or cloud disks. When it comes to deductions and billing, the security of data and files is particularly important. The ARM9 core board used in the "Mobile Payment for Public Transportation-Public Transport POS" solution of ZLG Zhiyuan Electronics adopts a dual backup file system and UPS power-off protection design to ensure the reliability of deduction data.

Figure 10 dual file system backup
Pet Anti Blue Light Film,Blue Light Screen Protector,Anti Blue Light Screen Protector,High Quality Laptop Screen Protector
Guangdong magic Electronic Limited , https://www.magicmax.cc