As the core support of the Internet, routing systems and theories urgently need to be further expanded and improved under the current network requirements. The future routing mechanism should have new features, so that the network can adapt to the increase in size and has good scalability; so that network users and operators have greater operating space and better flexibility; so that the network can fully It has better security against various network attacks; it enables the network to meet the needs of different businesses and has better service quality assurance. These key points have been recognized by more and more researchers. To this end, governments or research institutions around the world are formulating and implementing corresponding research plans, such as the GENI [1] and FIND [2] plans of the United States, the FIRE [3] plan of the European Union, and China ’s national high-tech research and development plan ( "863") and the National Key Basic Research and Development Plan ("973"), etc., trying to establish a new routing system theory and mechanism to make the future network fully meet the above needs.
1 Research on routing theory
One of the current studies on routing theory is first reflected in the routing architecture, focusing on solving the scalability problem of routing scale. To this end, the Internet Architecture Board (IAB) held the first "Routing and Address Working Group Meeting" in the Netherlands in October 2006. The meeting focused on discussing and determining the main factors that caused the problem of Internet routing scalability, and formed a clear document describing the problem of Internet routing scalability. This document analyzed several important reasons that led to the rapid growth of the global routing table and hindered router technology. The constraints of rapid development and the limitations of the Internet address structure. This document has officially become the RFC standard (RFC4984) in September 2007 [4].
At present, the Internet Research Task Force IRTF has established a routing research working group RRG, which mainly conducts research on Internet routing scalability. Current proposals in the RRG working group include AIRA, APT, CRIO, LISP, IPvLX, IVIP, Six / One, TAMARA, TRRP, etc. [5]. Throughout these research projects, the main core idea is to separate the identity signs of the nodes in the communication from the position signs, to solve the limitations of the traditional Internet IP address semantic overload, but only to the extent of changes in the existing network routing mechanism The difference. However, various technical solutions in the RRG working group are still at the discussion stage, lacking the necessary tests or simulations to support them.
In addition, there are NIRA [6], HLP [7], ROFL [8], AIP [9] and other proposals to solve the current problem of scalable Internet routing. NIRA provides a mechanism for hosts to choose different routing paths through different addresses. Through strict hierarchical address allocation strategies, NIRA can improve the scalability of routing. HLP is a routing protocol proposed as an alternative to BGP. It uses both link state and path vectors. It is a hybrid hierarchical routing protocol that can solve the problem of routing scalability to a certain extent. ROFL is a novel routing method based entirely on flat labels, and its effectiveness and practicality need to be further studied and verified. AIP uses a self-certified address hierarchy to try to solve network spoofing and routing security issues, but it is still in the discussion and research stage.
Research on traditional routing theory and technology has always been a hotspot in academic circles. The current research mainly reflects the following aspects:
(1) Research on routing security
At the beginning of the design of the existing routing protocols in the Internet, only one aspect of the network purpose was considered, that is, to provide routing reachability information for nodes or applications in the network, and the interactive transmission of this routing reachability information was established The network nodes are under the assumption of a mutually trusted group environment, and this assumption is no longer true in existing networks. The occurrence of a large number of routing security incidents on the existing Internet makes people have to reconsider the security of the routing mechanism. As early as 2002, the literature [10] pointed out the security defects of the inter-domain routing protocol BGP. Although S-BGP [11], soBGP [12], etc., have been proposed to improve the security of BGP, they have not been implemented yet.
(2) Research on routing reliability
Existing Internet routing protocols can only find a single "best" path to a destination for a given prefix. When a node of the network is under attack or a link fails, the existing routing protocol does not have a good protection mechanism and rapid recovery capability, and it is difficult to provide stable and reliable network services. In terms of routing reliability research, literature [13] and literature [14] provide fast rerouting and multi-topology routing mechanisms, respectively; literature [15] has carried out aspects such as avoiding failed nodes and providing inter-domain routing diversity. Exploratory research; literature [16] gives a path diversity program for users to choose. These work points out the way forward for the research of routing reliability.
(3) Research on controllability and controllability of routing
Existing routing mechanisms may cause network interruptions such as the interruption of individual nodes caused by the breakdown of individual nodes, the disorder of routing caused by the addition of individual nodes or systems, the indiscriminate use of bandwidth by P2P traffic, the spread of various network viruses and the network resources caused by attacks Irregular network behaviors such as shortages are difficult to detect in a timely manner, quickly locate and track, and handle irregular network behaviors in a timely and reasonable manner; in addition, the large number of network nodes and the large scale also bring certain complexity to network configuration management. Literature [17] has studied the detection technology of inter-domain routing traffic hijacking that may exist in the network. Literature [18] gives a method for deriving the fault location of the enterprise network. Literature [19] proposes to use a special channel for network routing. management. Nonetheless, the controllability and controllability of routing has not yet formed an effective solution, and the supervision and efficient configuration mechanism of the routing mechanism in the future needs to be improved.
(4) Research on routing service quality
The existing Internet provides a "best effort" forwarding service. Under this service model, all business flows are fairly treated with "equal treatment" of network resources, and service quality requirements such as reliability and delay of business flow transmission There is no guarantee. In this regard, the IETF has successively proposed two service quality architectures, integrated service [20] and differentiated service [21], but these two solutions have their own deficiencies in scalability and fairness. Multiprotocol Label Switching (MPLS) [22] seamlessly integrates the simplicity of IP routing control and Layer 2 switching, and provides a high-speed, secure, multi-service unified network platform without changing the user ’s existing network . Although MPLS is widely used at present, its deficiencies in network transmission efficiency, network compatibility, configuration complexity, network cost, and service quality granularity are not enough to meet the current development requirements of multiple services.
In short, the current network routing mechanism researches on network credibility issues such as security, reliability, controllability, and management. The above-mentioned research programs mainly stay at a local goal of theory or application. What they have done is only the existing The patching of network routing trust problems has not yet formed a complete and systematic routing theory system that can fully meet the needs of users and networks, so it has not been able to fundamentally solve the problem of network routing trust.
2 Connotation of trusted routing
The concept of a trusted system was first proposed by Professor JP Anderson in the early 1970s, and was initially only used to describe the availability, integrity and confidentiality of information. Later, when it was applied to the network, the traditional routing mechanism exposed many problems in terms of security, reliability, controllability and other aspects. When we say that a system is credible, it usually means that the behavior and results of the system are predictable. Broadly speaking, trusted routing refers to a network that can provide users with safe, reliable, controllable, and manageable routes that meet user network service quality requirements in accordance with the expectations of users and network operators in any situation. To this end, the design requirements for trusted routing should include the following:
(1) Space isolation protection
It is necessary to distinguish between the access network and the core network, introduce different sign spaces, deploy border routing equipment between the core network and the access network, and provide sign-based mapping services, so that the change of the routing scale is independent of the size of the user network. Make the network more scalable, and at the same time fully guarantee the security of the core network equipment.
(2) Separation of identity and location
The identity and location information of the node should be separated, and a unified identity and location mapping mechanism should be established throughout the network to achieve safe and fast online management of the mapping information, to achieve privacy protection of the node location and continuous connection in the case of node movement, so as to satisfy users Increasing demand for mobility and privacy.
(3) Trusted routing addressing
The necessary identity authentication mechanism and the secure transmission mechanism of routing messages should be adopted to ensure the authenticity of the routing node ’s identity and the confidentiality and integrity of the routing reachability information; to realize the multiplexing mechanism between the network routing nodes and provide the routing Backup and rapid recovery capabilities, so that the network has a more secure and reliable service capability.
(4) Service quality assurance
A combination of centralized and distributed methods should be used to fully extract the network resource utilization status, and to provide different-level differentiated routes to meet the needs of different business applications and their service quality requirements.
(5) Network security protection
A distributed safety detection and protection system for the entire network should be established to achieve comprehensive analysis of network transmission and network status, while providing certain network error diagnosis capabilities and effective safety management mechanisms and strategies to make the network routing mechanism better Controllability.
3 Trusted routing reference mechanism
3.1 Trusted routing architecture model
Based on the above research on trusted routing theory and technology, this section proposes a trusted routing architecture model. The new structure uses different network logos to represent the identity information and location information of the host, and the single address space of the original IP network Divided into two different logo spaces, different routing methods are used in the two logo spaces, and a relatively independent routing space is formed, and addressing and routing are completed between the two logo (routing) spaces through the method of logo mapping. The new network structure is divided into an access network and a core network, and contains two kinds of signs: an access sign and a switching route sign. The access mark represents the identity information of the terminal and can only be used in the access network, while the exchange routing mark represents the location information of the terminal and can only be used in the core layer. The new routing architecture uses the "indirect communication" mode to connect the two logo spaces: the access network uses the access logo to forward data, and the core network uses an internal exchange routing logo to replace the access logo forwarding; the access network is responsible for various communications For terminal access, the core network performs control management and exchange of routes. The new trusted routing architecture is shown in Figure 1.
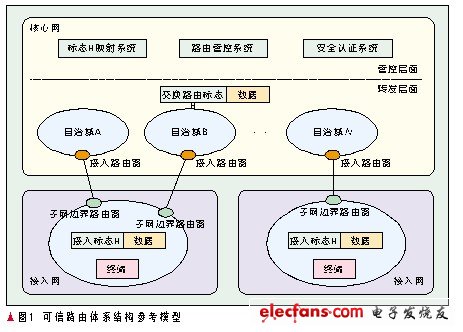
In the above reference model of trusted routing architecture, the separation of the access network and the core network makes the dynamic changes of the access network not appear on the core network, which ensures the relative stability of the core network. , Traffic engineering, etc. will not cause the growth and instability of the core network routing table. The access mark representing the user ’s identity will not be propagated on the core network, so that other users cannot analyze the user ’s identity by intercepting the information on the core network, ensuring the privacy of the user ’s identity; it is also impossible to intercept their information through the user ’s identity. Ensure the security of user information. At the same time, the terminals in the access network cannot know the switching route signs of network facilities in the core network or the switching route signs of other terminals; The attack guarantees the security of the core network facilities and data. The new routing structure is still divided into intra-domain routing and inter-domain routing.
The M8 cable is also called the M8 connector (with cable), because the connection wire above the sensor is most often used with the M8 connector (with cable), that is, the M8 connector - with cable series.
The basic performance of M8 connectors can be divided into three categories: mechanical properties, electrical properties and environmental properties.
M8 cable is mainly used in outdoor light box, electronic instrumentation, electronic machinery, communications, construction machinery, steel production equipment, power equipment, mining machinery, Sensors, solenoid valves, etc.


M8 male connection cable , M8 female connection cable,M8 3 pin connector cable,M8 4 pin connector cable,M8 male to female cable
Kunshan SVL Electric Co.,Ltd , https://www.svlelectric.com